What is Ransomware?
Ransomware is a type of malware that infects your computer
network and other devices. Once infected, your data is locked
and encrypted, making it unusable and inaccessible until a
ransom payment is received.
While a majority of ransomware encrypts data on the victim’s
server until the ransom is paid, we have observed an increase
in double-extortion methods that take it a step further by
copying the stolen data to a cybercriminal’s server.
This means, even if a ransom is paid, the victim’s data has
already been exposed and will likely be exploited or sold
illegally on the dark web. Therefore, backing up data is not
enough for businesses to mitigate the threat.
It is critical that business leaders begin taking a proactive
approach to prevent these attacks from compromising,
releasing, and destroying sensitive data.
How do users get Ransomware?
There are a number of ways in which ransomware is spread,
including malicious email attachments and URLs. A file
can be delivered in a variety of formats including Word
documents, Excel spreadsheets, PDFs, zip files, and more.
When a user clicks on a malicious link or file, ransomware can immediately deploy or remain dormant for days, weeks, or even months before encrypting a victim’s files.
While you may think it’s easy to spot a malicious email,
cybercriminals are becoming more sophisticated and often
conduct extensive research on their target. As a result,
ransomware groups are able to deceive users with very
credible and believable emails.
If you are interested in learning more about the common
ways in which ransomware is spread, please continue
reading below.

By 2031, ransomware is expected to attack a business,
consumer, or device every 2 seconds, and will cost victims
approximately $265 billion (USD) globally, according to
Cybersecurity Ventures’ 2022 Ransomware Market Report.
Cybersecurity Ventures’ 2022 Ransomware Market Report.
Cybersecurity measures have taken a giant leap in recent years to keep up with the ever-growing number of cyber threats. Some roducts make for excellent antiviruses or response tactics, but it’s time to start thinking about how you will prevent cyber attacks from occurring in the first place.
According to Score, ransomware ranked number one among the top five cybersecurity threats to small businesses in 2022, with business email compromise (BEC) scams right behind it. The threat of human error that leads to employees opening malicious documents
and links in BEC scams is why a proactive solution to prevent ransomware from spreading throughout your device or even your network is the missing piece to your cybersecurity stack.
Torchsec’s solutions are curated to provide the proactive security and defenses your organization needs to handle a slip in human error that could cause devastating harm to any SMB. These solutions stop malware from hurting your organization before it gets the chance.
This document aims to give you an overview of the current cybersecurity landscape and to help you understand how an endpoint security solution, like Torchsec’s ThreatLocker, will help keep your business safe and secure.
Types of Malware
Malware is a piece of malicious software designed by cybercriminals to steal your data and carry out other nefarious behaviors. Malware can be spread in many ways, including phishing, malicious URLs, downloads, browser extensions, and more.

Ransomware is a type of malware that infects your computer network and other devices. Once infected, your data is locked and encrypted, making it unusable and inaccessible until a ransom payment is received.

A Virus is another form of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code

Like viruses, worms replicate in order to spread to other computers over a network. In the process, they cause harm by destroying files and data.

A Trojan is a form of malware that can be used to steal financial information or install ransomware. This is one of the most dangerous forms of malware, as it is often disguised as legitimate software

This malware records all of the keystrokes on your keyboard. This sends all of your sensitive information, including credit cards, passwords and other user credentials to a cybercriminal.

Spyware is malicious software designed to enter your device, gather your information, and forward it to a third-party without your consent. This software is used to profit from stolen data.
Ransomware attacks are constantly making news headlines. However, the stories you hear often focus on large enterprise organizations.
Today, cybercriminals frequently target small to mediumsized organizations, which are often more vulnerable to these attacks. Additionally, ransomware attacks can destroy a business as a result of the financial burden inflicted from direct and indirect damage.
In addition to the ransom payout, you must factor in downtime, reputational damage, data loss, and other repercussions that may follow.

In 2022, the average ransom payment was over $810,000 (USD). Only a portion of the average total $4.5 million (USD) incurred costs, including demand payments.

On the dark web, the average cost of stolen documents and accounting data is about $1,285. Victims who have had their organizations records compromised are often left grappling with the effects years later.

It is estimated that the average amount of time a ransomware attack lasts, including the time it takes to identify the attack and remediate and restore systems, is about 50 days.
ThreatLocker® is a Zero Trust endpoint protection platform that provides enterprise-level cybersecurity to organizations globally. Instead of relying heavily on detection methods and chasing threats, the ThreatLocker® solutions block everything that is not explicitly trusted and limit actions to only what is needed.
“Zero Trust security is much more effective than detection tools.” The
ThreatLocker® Zero Trust philosophy extends beyond Allowlisting to
incorporate controlling what permitted applications can do, what storage areas can be accessed and how, and what network connections can be made. Denies and allows are recorded in real time in a Unified Audit to assist with compliance and ThreatLocker® Ops utilizes this real-time data to alert you of any blocked malicious action.
The ThreatLocker® endpoint protection platform is designed to be
easy to use and integrate seamlessly into existing IT environments.
Our innovative Learning Mode and rapid response time of the 24/7/365 Cyber Hero Support Team makes onboarding and implementing ThreatLocker® a streamlined process.

Application Allowlisting denies all applications from running except those that are explicitly allowed. This means untrusted software, including ransomware and other malware; will be denied by default.
When the agent is first installed, it operates in Learning Mode. During this period, all applications and their dependencies found on the computer are cataloged and polices are created to permit them. After the learning period, the IT administrator can review the list of applications, remove those that are not required, and secure the computer. Once the computer is secured, any untrusted applications, script or library that try to execute will be denied. The user can request new software
from the IT administrator and it can be approved in 60 seconds.
Application Allowlisting has long been considered the gold standard in protecting businesses from known and unknown malware. Unlike antivirus, Application Allowlisting puts you in control of what software, scripts, executables, and libraries can run on your endpoints and servers. This approach not only stops malicious software, but also stops other unpermitted applications from running. This process greatly minimizes cyber threats and other rogue applications running on your network.
Whitelisting blocks all untrusted applications, however, it will not stop an attacker from weaponizing tools and applications against you. ThreatLocker’s proprietary Ringfencing™ solution goes beyond blocking untrusted applications. Continue reading to learn more.

Using the ThreatLocker® solution, you can deny any application from running on your device that is not a part of the allowlist. This helps to mitigate and stop cyberattacks from happening on your devices or across your network.

A powerful firewall-like policy engine that allows you to permit, deny or restrict application access at a granular level.

Permit access to applications for a specified amount of time. Automatically block the application after the policy has expired.

ThreatLocker® automatically adds new hashes when application and system updates are released, allowing your applications to update without interference while preventing updates from being blocked.
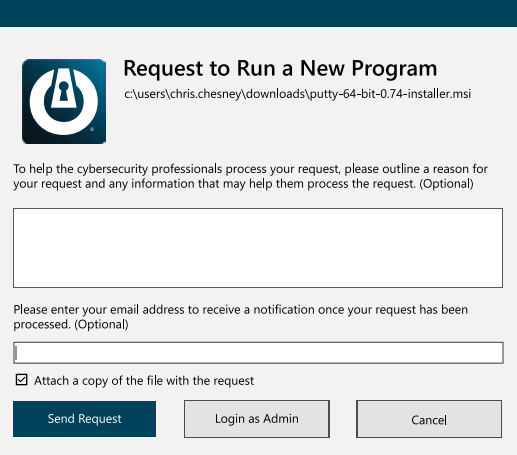
The approval center allows you to easily control what is permitted to run on your computer with a 30-second single click approval.
Users have the ability to request permission or ignore notifications for unapproved applications.
Ringfencing™ controls what applications are able to do once they are running. By limiting what software can do, ThreatLocker® can reduce the likelihood of an exploit being successful or an attacker weaponizing legitimate tools such as PowerShell.
Ringfencing™ allows you to control how applications can interact with other applications. For example, while both Microsoft Word and PowerShell may be permitted, Ringfencing™ will prevent Microsoft Word from being able to call PowerShell, thus preventing an attempted exploit of a vulnerability such as the Follina vulnerability from being successful.
Under normal operations, all applications permitted on an endpoint have the same access as the operating user: data, applications, the network, and the registry. If compromised, an attacker can use the application to steal or encrypt files, abuse legitimate tools, communicate with malicious IPs, and make changes to the registry. Ringfencing™ allows you to create boundaries to permit applications access to only what they need.
When you first deploy Ringfencing™, your device will automatically be aligned with the default ThreatLocker® policies. These policies are then automatically applied to a list of known applications such as Microsoft Office, PowerShell, or Zoom. The default policies aim to provide a baseline level of protection for all endpoints. Policies can be created and changed to fit any environment. Our dedicated Cyber Hero Team is always on hand to support any requests, 24/7/365.

Stop fileless malware by limiting what applications are allowed to do.

Stop applications from interacting with other applications, network resources, registry keys, files, and more.
Limit application attacks like application hopping by limiting what applications can access.

The average computer has over 500 applications, and only a handful of those need to access your files. With Ringfencing™, you can choose which applications need to see which files.
*Verizon Data Breach Investigation Report, 2022
Attacks against web applications are now the fastest-
growing category. At ThreatLocker®, protecting your
applications from ransomware and other malicious
threats is one of our top security concerns.
Elevation Control enables users to run specific applications as a local administrator, even when they do not have local admin privileges. Elevation Control puts IT administrators in the driving seat, enabling them to control exactly what applications can run as a local admin without giving users local admin rights.
When ThreatLocker® is first deployed, all existing applications are learned. Administrators can review the applications and select which can be run as a local administrator. Once enabled, user can run the software as a local administrator without entering any credentials.
Local administrator credentials are a sought-after target for cybercriminals. An attacker who has gained access to a user’s endpoint with local admin rights can impersonate other loggedon users or exploit tools locally, potentially pivoting into the entire network. Elevation Control enables IT administrators to eliminate the possibility of these credentials being hijacked and used against them without hampering productivity.

Gives you the ability to approve specific applications to run as an administrator, even if the user is not a local administrator.
Users can request permission to elevate applications and attach files and notes to support their requests.

Enables you to set durations for how long users are allowed access to specific applications by granting either temporary or permanent access.

Ringfencing™ ensures that users cannot jump to infiltrate connected applications within the network once applications are elevated.
Storage Control provides policy-driven control over storage devices, whether the storage device is a local folder, a network share, or external storage. ThreatLocker® Storage Control allows granular policies to be set, which could be as simple as blocking USB drives, or as detailed as blocking access to your backup share, except when accessed by your backup application.
Unified Audit provides a central log of all storage access by users on the network and those working remotely, right down to the files that were copied and the device’s serial number.
Policies can be created to permit or deny access to storage locations based on the user, window of time, type of file, and the application in use. When a storage device or location is blocked, a user will be presented with a pop-up where they can request access to the device or location. The administrator can then permit the storage device in as little as 60 seconds.
As a high-value target for threat actors, protecting data from unwanted access is important. ThreatLocker® Storage Control enables the creation of granular policies to permit and deny access to network shares, local folders, and external storage by specific users or applications, and to enforce encryption on external storage devices.

A full detailed audit of all file access on USB, Network, and Local Hard Drives is centrally accessible within minutes of a file being opened.

These policies allow or deny access to storage based on user, time, applications, and more.

Upon denial due to policy, a pop-up appears to provide the user an option to request access to the storage device.

USB Policies allow access based on device serial number, vendor, and/ or file type.
ThreatLocker® Network Control is an endpoint and server firewall that enables you to have total control over network traffic, which ultimately helps you to protect your devices. Using custom-built policies, you can allow granular access based on IP address, specific keywords, or even agent authentication or dynamic ACLs.
The corporate firewall is no more. Users are not only working from the office but also remotely, meaning that the network we all utilize has quickly become the internet. This dissolution of the perimeter leaves devices and data vulnerable and exposed to cyber threats. This is why you need controls on network traffic in place to protect your device and, by extension, your data. You can achieve this by implementing a Network Control solution.
Network Control enables you to set firewall policies for all endpoints from a single location. Control network traffic using on-demand port control. Once a connection request is received, ThreatLocker® checks to see if the requesting endpoint is permitted to make that connection. If permission is verified, ThreatLocker® will open the requested port on the device. Unapproved devices will not have visibility of the open port. Once an authorized device is no longer using the open port, it will automatically close within 5 minutes.

Using global and granular policies, Network Control allows users to configure network access to endpoints.

The cloud-managed solution provides customers with a centralized view of endpoint policies and network traffic across your organization.

Network Control enables users to deny all traffic to published servers while only allowing a single computer by IP address or dynamically using a keyword. This is great for a user who is often traveling.

Ensure rogue devices on your network cannot access your servers or endpoints with Dynamic ACLs.
(380) 900-7099 Call/Text
20 East Main Street, Centerburg, OH 43011
Website by Donstudio.com
